A new business email compromise (BEC) based campaign using compromised LinkedIn profiles to deliver content was identified by the team at 7 Elements today (7th November 2019).
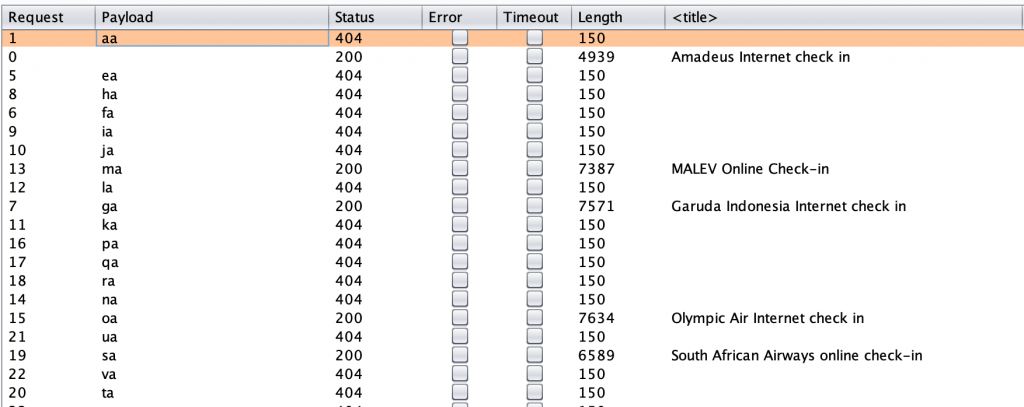
The campaign uses LinkedIn email to deliver a message enticing the user to follow a link, which would result in the user being prompted for credentials. The phishing kit is complex in nature, supporting multiple email providers such as Office 365, Gmail and Hotmail. Analysis of the kit also showed inbuilt defensive capabilities designed to disrupt investigation by security vendors.
The following video demonstrates how an end user could be enticed to provide their email credentials via this campaign:
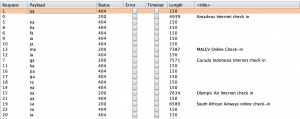
The campaign started at 07:03hrs on the 7th November 2019 and was still active at the point of publishing this advisory at 21:45hrs (14hrs later). In this period there had been over 1,900 visits to the phishing site, with 670 (35%) of those from the UK.
More detailed analysis of the phishing kit will follow in a later post.