Recap
The MS-14-064 patch last week addressed several vulnerabilities that could allow for remote code execution in applications using the SChannel Security Service Provider. The vulnerabilities (including cve-2014-6332) affect distributions of Microsoft Operating Systems from Windows 95 IE 3.0 to Windows 10 IE 11. More background can be found in our earlier blog post and in summary, our advice was to patch your systems now without delay.
That was last week, where are we now?
Exploit: All The Things!
“As both security researchers and blackhats are inevitably working toward creating a workable exploit, enterprises need to apply the patch released to all applicable systems without delay.”
The promise of exploitation was kept by @yuange who released an exploit that allowed an attacker to remotely open notepad on a victim machine. This exploit was then adapted by Rik van Duijn. This adaptation executes Powershell in order to inject payloads directly into memory and as an added benefit, using Powershell maximises the chances of successfully bypassing anti-virus software (Powershell is often whitelisted as a trusted application).
The proof of concept code injected a “reverse_tcp” meterpreter payload into memory, resulting in a shell from which system commands could be executed. Rik van Duijn has released this proof of concept as a Metasploit module to allow a multitude of further payloads to be delivered. This also has the associated impact of making the exploit easier to deliver, therefore increasing the overall likelihood that systems vulnerable to cve-2014-6332 will be targeted.
Meanwhile, another proof of concept has been published by Immunity Inc, this SChannel exploit using their CANVAS tool, may allow remote command execution(RCE) via the Windows remote desktop protocol(RDP).
Vulnerability Checking
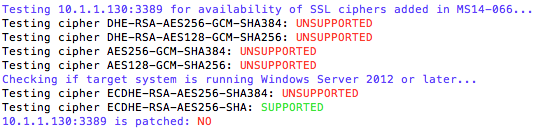
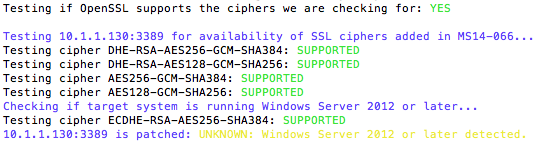
Anexia have released a tool that will check if a Windows operating system is vulnerable. This tool conducts behavioural analysis based upon available SSL ciphers. Their script checks to see if the target system has been patched or not. It does this by checking if the system supports four new SSL ciphers that were introduced by MS14-066.
To run the tool you need to specify a target IP address and a port that with a service running that listens for connectable SSL connections. If the script takes too long or times-out then it is likely that a firewall is blocking the connection, you are connecting to the workstation indirectly or that no service is listening.
Example:
Vulnerable System Result:
Patched System Result:
Disclaimer
While testing in our labs was accurate, Anexia warn that the script may, in certain cases, generate false negatives/positives and should be used as a hint for further investigation, do not take results of this script on faith.
Inevitable XP Swansong
Microsoft have not indicated plans to patch Windows XP, therefore it would be wise to decommission any vulnerable machines or where this is currently not possible, segregate legacy environments to limit potential exposure.
Links
http://blog.beyondtrust.com/triggering-ms14-066
https://forsec.nl/2014/11/cve-2014-6332-internet-explorer-msf-module/
http://itsecurityguru.org/microsoft-patches-winshock-flaw-amid-attack-reports/#.VGoZModLGiA