Whilst investigating the technical feasibility of scraping Facebook Marketplace to aid in the recovery of stolen goods, it was possible to identify sensitive data disclosing the exact location of the sale item.
The Location data contained within the JSON responses of adverts made through the Facebook Mobile Application, seemed… a little specific. Which goes against the generalised location data displayed to the end user.
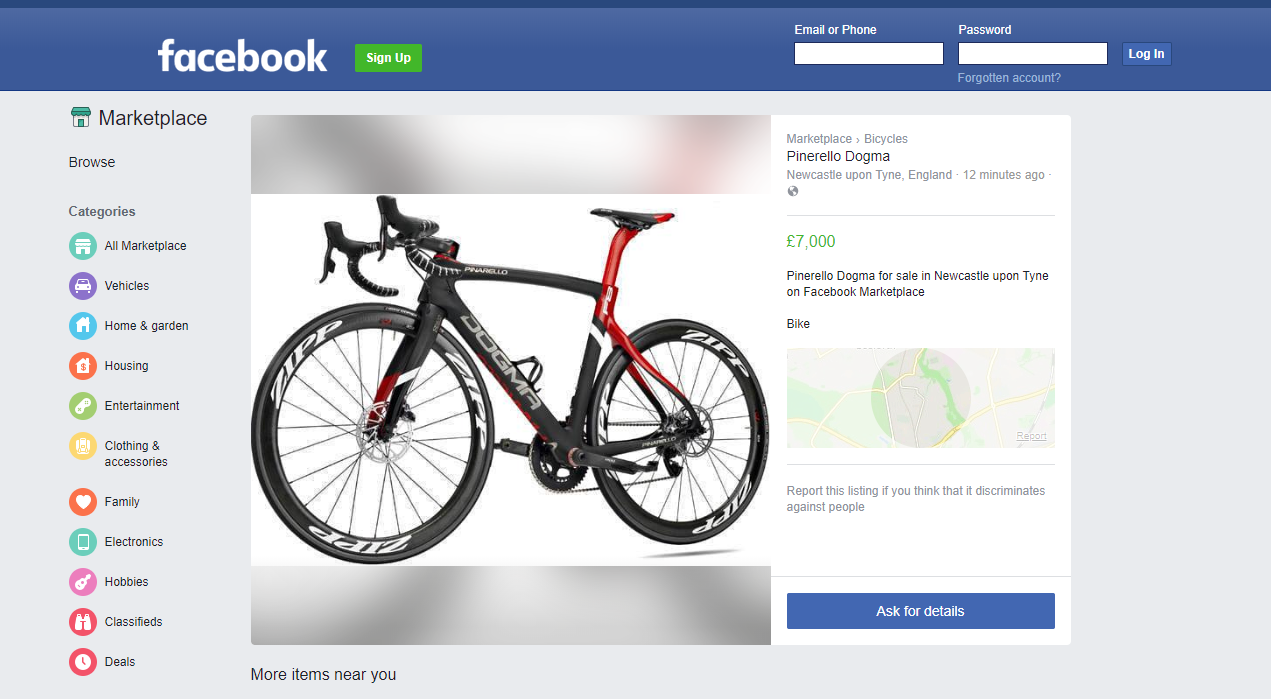
Nice bike, glad Facebook fuzzes that location. Otherwise bad people could do bad things.
Digging Deeper
I quickly made my own advert for a random item/address using the mobile application, in order to verify that what I was seeing.
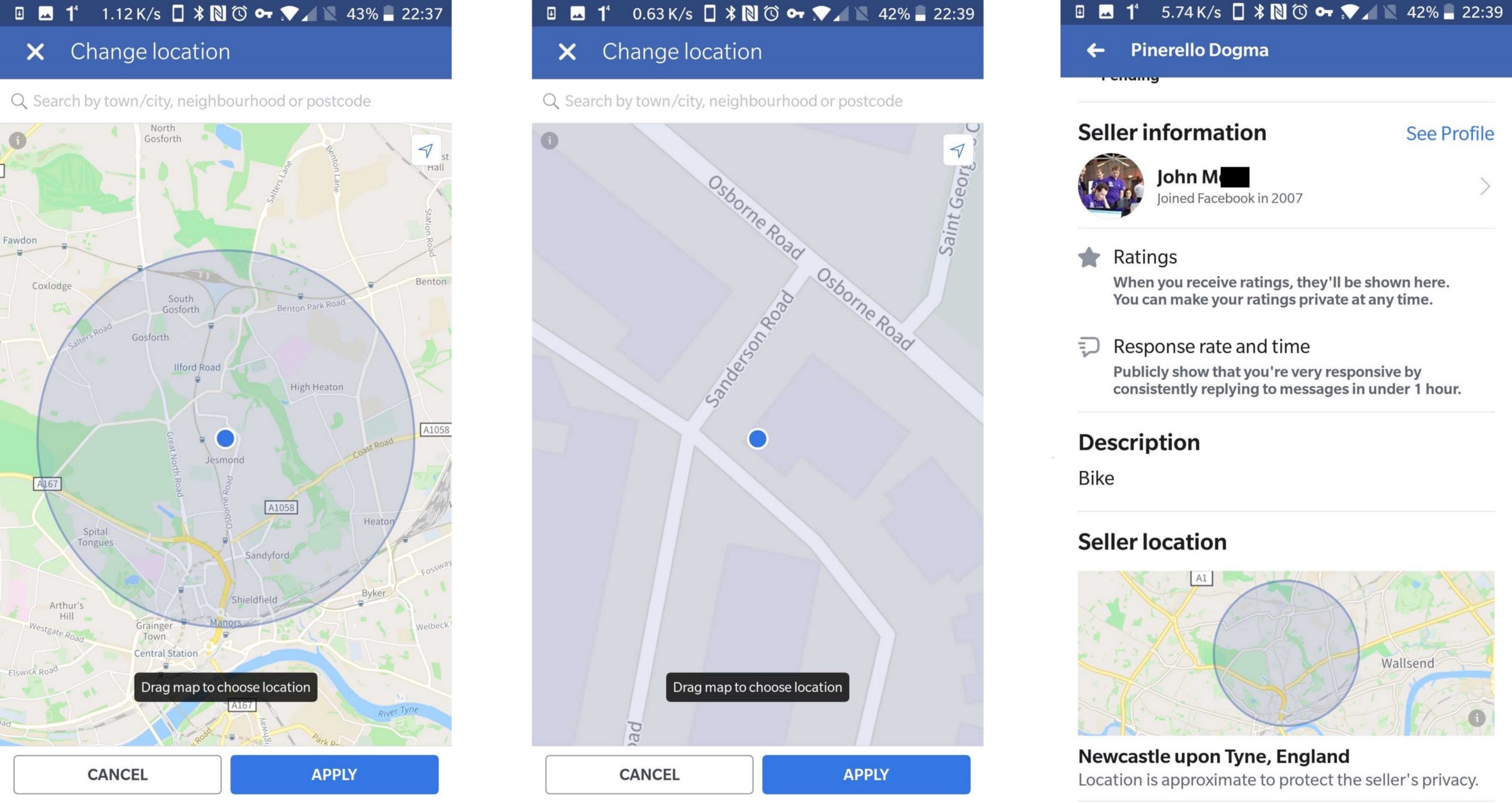
“Location is approximate to protect the seller’s privacy”… Yeah about that
Back on the web application I took a closer look at the requests generated when accessing the bicycles advert (as an unauthenticated user). I soon was able to confirm the request facebook.com/api/graphql, was revealing detailed location information in a JSON response.
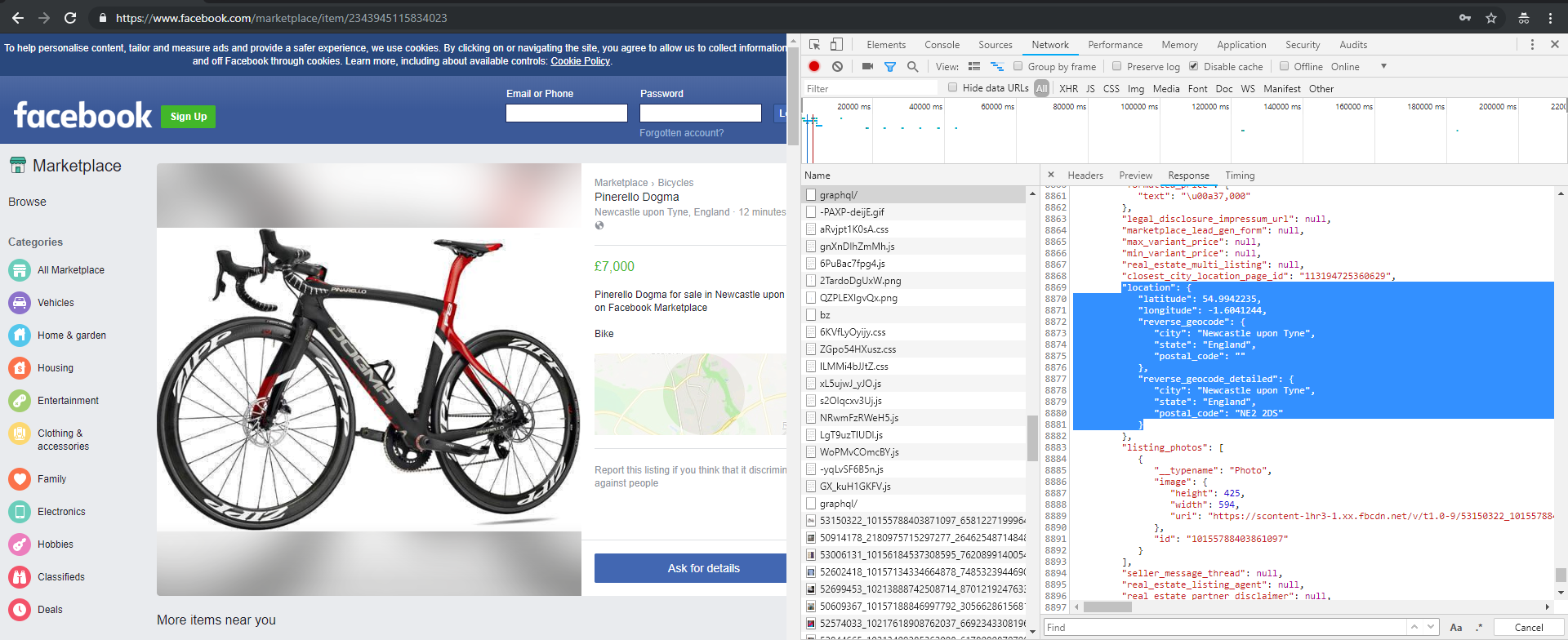
The GraphQL API request when the advert is accessed unauthenticated. If you’re feeling lazy just zoom in on the centre of the circle.
For those that can’t read tiny writing the highlighted JSON section reads…
"location": {
"latitude": 54.9942235,
"longitude": -1.6041244,
"reverse_geocode": {
"city": "Newcastle upon Tyne",
"state": "England",
"postal_code": ""
},
"reverse_geocode_detailed": {
"city": "Newcastle upon Tyne",
"state": "England",
"postal_code": "NE2 2DS"
}
}
On checking the latitude/longitude on Google I found it pin pointed the exact location I pinned when making the advert. This would make it easy for anyone malicious to identify the location of that “£7,000 bike” almost down to the meter. It’s also probably not the best idea for the full postcode to be available publicly as well given it wouldn’t take much to find an address based on that and the other information available (i.e the sellers full name).
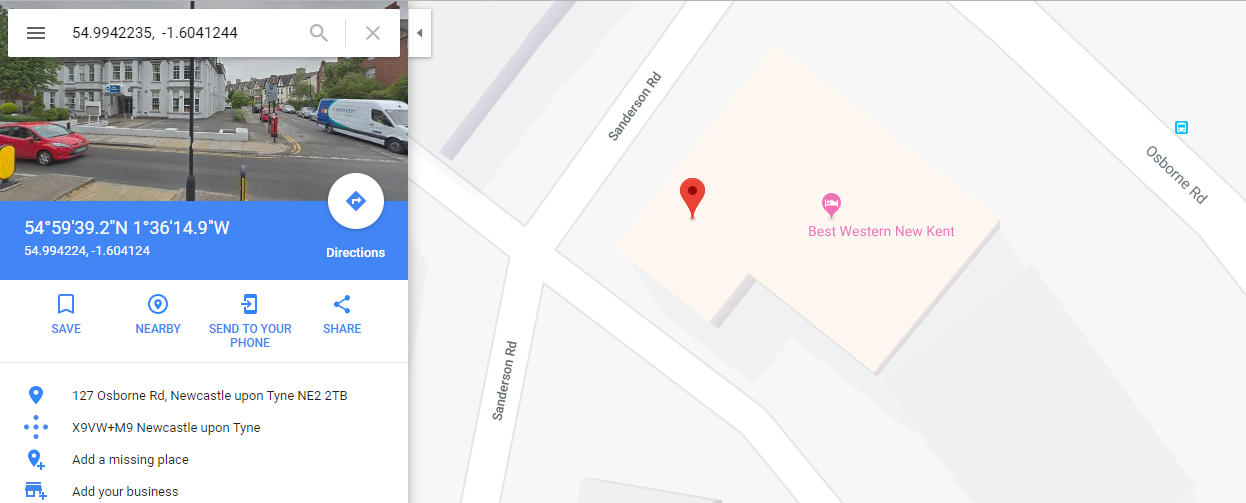
Isn’t that the exact location I pinned in the above screenshots?
So what’s wrong with that?
Whilst the user has to pin their exact address every bit of Facebooks UI during the item listing process suggests this is fine and will be fuzzed for anyone viewing the advert. The circle whilst pinning suggests the exact address/point will be fuzzed, the text on the adverts says the sellers location is approximate, there’s even functionality to pin your exact location using GPS so I don’t believe it’s intended that the user fuzzes their location manually.
Furthermore, when I tried to submit a specific location using the Facebook web application I found that I was completely unable to drill down beyond the nearest suburb (trying both postcode or full address just didn’t work).
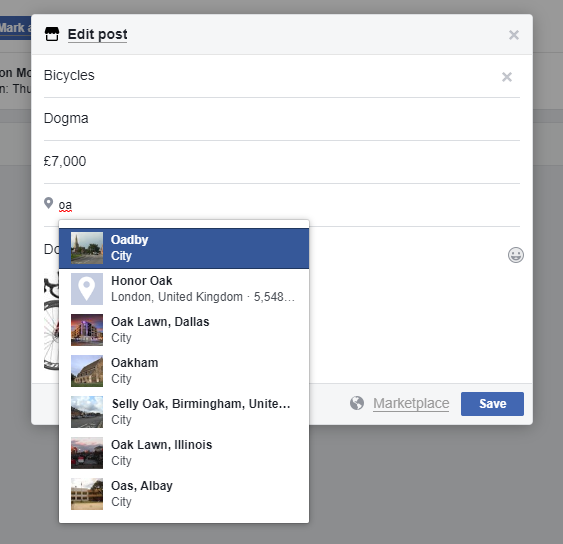
No way to get more specific than the nearest Facebook “Place” in the web application
Expected Behaviour?
I would’ve expected that Facebook would randomise the point to a location within the circle or snap to the nearest generic location like the web application. I would also have expected that Facebook only reveal the first 3/4 characters of the postcode and not the full thing. Indeed, when Facebook made the fix to prevent this information being leaked the above seems to be the approach they took and now when I try to add an advert it snaps to a local park.
Challenges of Responsible Disclosure
I quickly reported my findings to Facebook, originally highlighting the full postcode, this was rejected as they didn’t believe it to be a security vulnerability. I did some more investigation and found the exact situation this occurs along with the long/lat parameters and updated the report… Again it was quickly rejected. Feeling a little bit down, I talked to someone I know who works at Facebook, they were able to get someone to take a more depth look at what I was actually reporting and as a result the report was accepted. A fix was then quickly implemented after just over a week.
