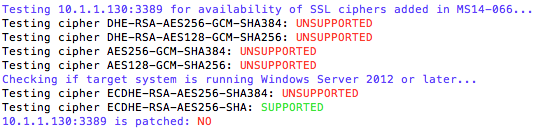
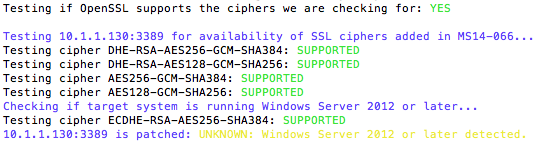
Creating a Strong SNMP Community String
To ensure that an attacker does not gain privileged or read access to your devices via a poorly configured SNMP community string, we would recommend that the following steps should be taken:
Follow similar guidance to mainstream password guidance.
• Use both upper and lower case
• Include one or more numerical digits
• Use special characters, e.g. @, #, $ etc.
• Prohibit use of words found in a dictionary
• Disallow passwords matching the format of calendar dates, license plate numbers, telephone numbers, or other common numbers
• Prohibit of use of company name or an abbreviation